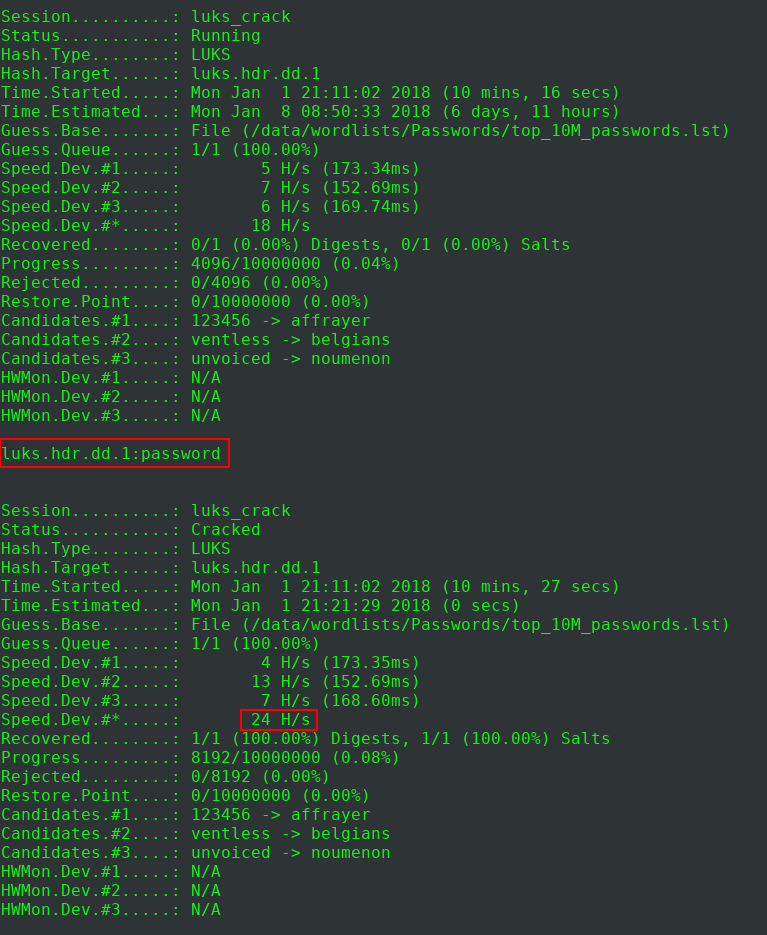
Time to crack a LUKS password from an encrypted block device.
To begin, we need to identify a LUKS encrypted device.
We can do this by using “cryptsetup”.
cryptsetup isLuks {block device}; echo $?;
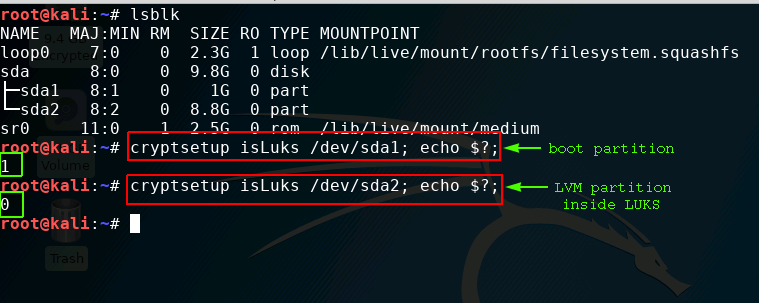
If it returns a 0. it is a LUKS device.
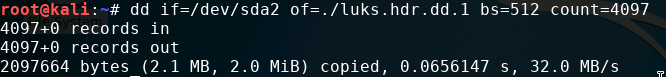
Next, we need to dump the header and a little bit of data.
dd if={luks device} of=luks.header bs=512 count=4097
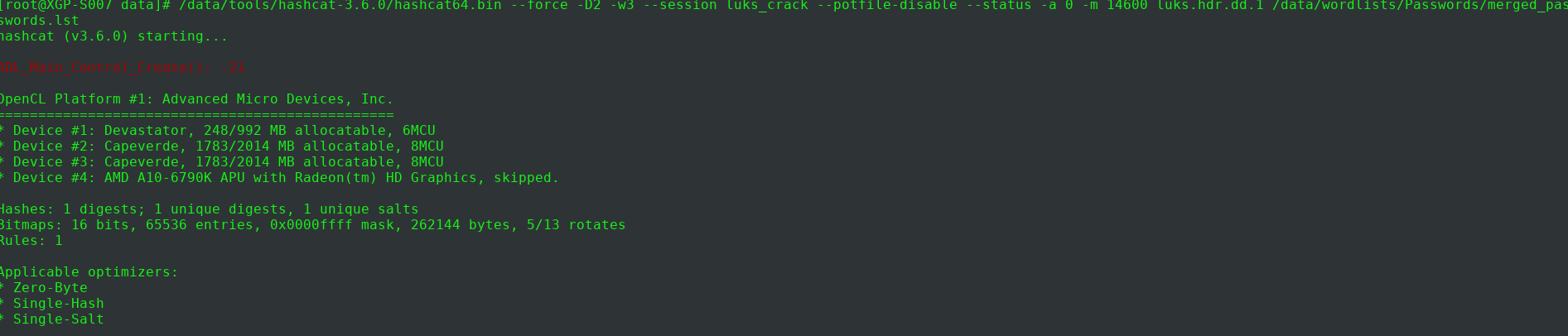
Now we are ready to start cracking with Hashcat.
The general Hashcat command for cracking LUKS is hashcat -a 0 -m 14600 {luks.header} {wordlist}
The cracking speed is very slow due to the number of iterations used when generating the master key of the encrypted device. Using a well-crafted wordlist is recommended.